Windows Azure: Improvements to Virtual Networks, Virtual Machines, Cloud Services and a new Ruby SDK
This morning we released some great enhancements to Windows Azure. These new capabilities include:
- Virtual Networks: New Point-to-Site Connectivity (very cool!), Software VPN Device and Dynamic DNS Support
- Virtual Machines: Remote PowerShell and Linux SSH provisioning enhancements
- Cloud Services: Enable Remote Desktop Support Dynamically on Web/Worker Roles
- Ruby SDK: A new Windows Azure SDK support for Ruby
All of these improvements are now available to start using immediately (note: some services are still in preview). Below are more details on them:
Virtual Networks: New Point-to-Site Connectivity and Software VPN Device support
Last week we announced the general availability of Virtual Network support as part of our IaaS release.
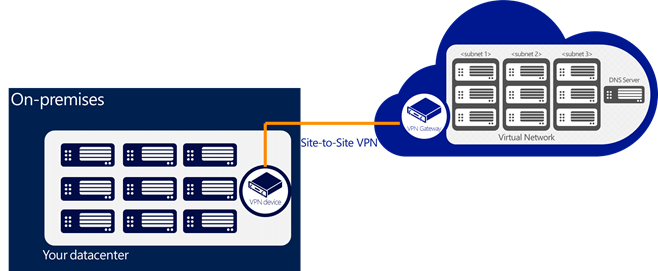
Virtual Networking allows you to create a private, isolated network in Windows Azure and treat it as an extension of your on-premises datacenter. For example, you can assign private IP addresses to virtual machines inside a virtual network, specify a DNS, and securely connect it to your on-premises infrastructure using a VPN device in a site-to-site manner.
Here’s a visual representation of a typical site-to-site scenario through a secure Site-To-Site VPN connection:
Today, we are excited to announce that we’re expanding the capabilities of Virtual Networks even further to enable three new scenarios:
New Point-To-Site Connectivity
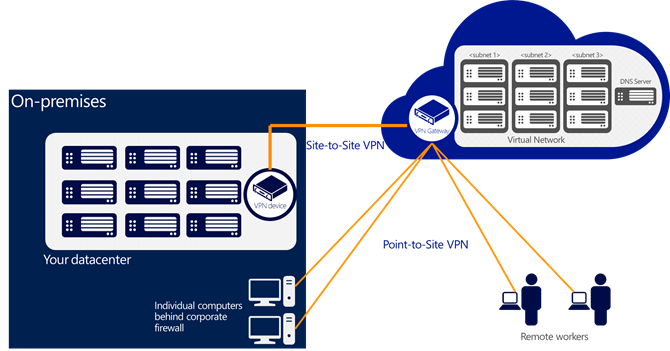
With today’s release we’ve added an awesome new feature that allows you to setup VPN connections between individual computers and a Windows Azure virtual network without the need for a VPN device. We call this feature Point-to-Site Virtual Private Networking. This feature greatly simplifies setting up secure connections between Windows Azure and client machines, whether from your office environment or from remote locations.
It is especially useful for developers who want to connect to a Windows Azure Virtual Network (and to the individual virtual machines within it) from either behind their corporate firewall or a remote location. Because it is point-to-site they do not need their IT staff to perform any activities to enable it, and no VPN hardware needs to be installed or configured. Instead you can just use the built-in Windows VPN client to tunnel to your Virtual Network in Windows Azure. This tunnel uses the Secure Sockets Tunneling Protocol (SSTP) and can automatically traverse firewalls and proxies, while giving you complete security.
Here’s a visual representation of the new point-to-site scenarios now enabled:
In addition to enabling developers to easily VPN to Windows Azure and directly connect to machines, the new Point-to-Site VPN support enables some other cool new scenarios:
- Small businesses (or departments within an enterprise) who don’t have existing VPN devices and/or network expertise to manage VPN devices can now rely on the Point-to-Site VPN feature to securely connect to their Azure deployments. Because the VPN software to connect is built-into Windows it is really easy to enable and use.
- You can quickly set up secure connections without the involvement from the network administrator, even if your computers are behind a corporate proxy or firewall. This is great for cases where you are at a customer site or working in a remote location (or a coffee shop).
How to Enable the Point-to-Site Functionality
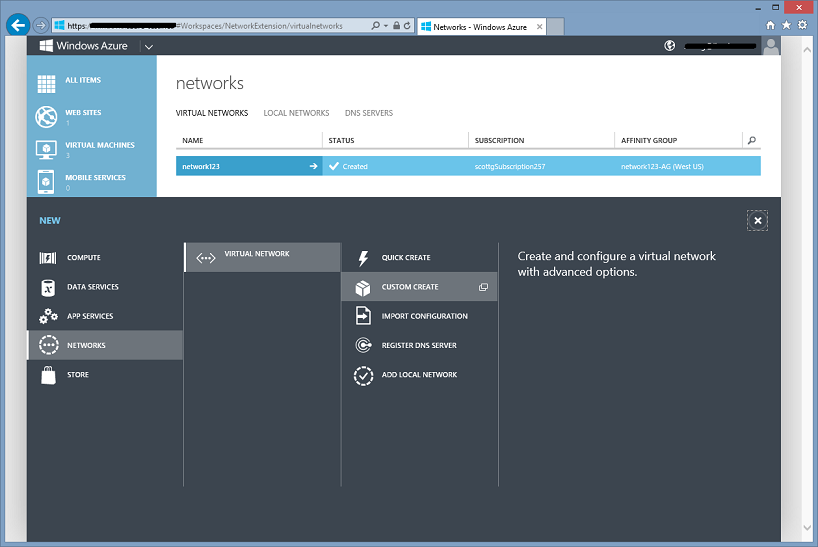
With today’s release we’ve updated the Virtual Network creation wizard in the Portal so that you can now configure it to enable both ‘Site-to-Site’ and ‘Point-to-Site’ VPN options. Create a Virtual Network using the “Custom Create” option to enable these options:
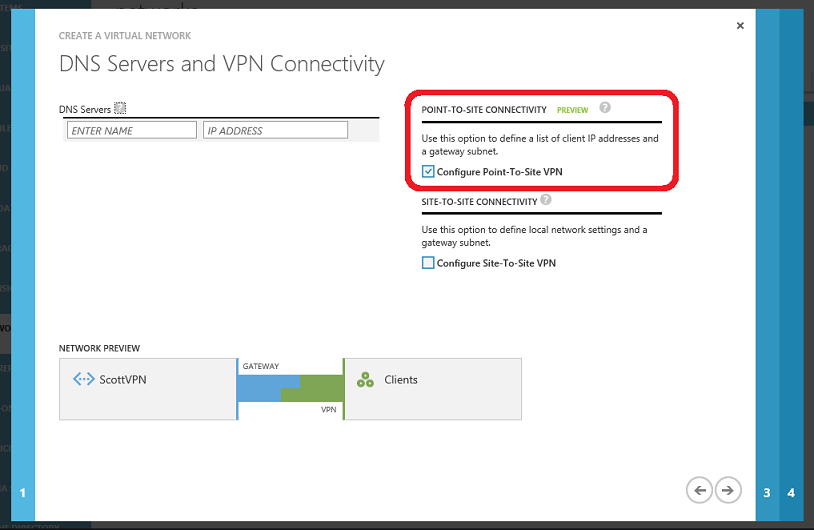
Within the Virtual Network Custom Create wizard you can now click a checkbox to enable either the Point-To-Site or Site-To-Site Connectivity options (or both at the same time):
On the following screens you can then specify the IP address space of your Virtual Network. Once the network is configured, you will create and upload a root certificate for your VPN clients, start the gateway, and then download the VPN client package. You can accomplish these steps using the “Quick Glance” commands on the Virtual Network dashboard as well as the “Create Gateway” button on the command-bar of the dashboard. Read this tutorial on how to “Configure a Point-to-Site VPN in the Management Portal” for detailed instructions on how to do this.
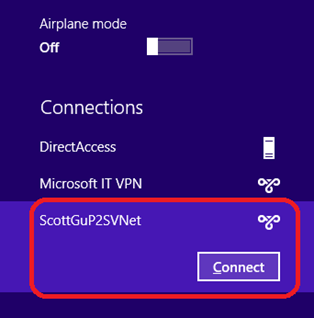
After you finish installing the VPN client package on your machine, you will see a new connection choice in your Windows Networks panel. Connecting to this will establish a secure VPN tunnel your Windows Azure Virtual Network:
Once you connect you will have full IP level access to all virtual machines and cloud services hosted in your Azure virtual network! No hardware needs to be installed to enable it, and it works behind firewalls and proxy servers. Additionally, with this feature, you don’t have to enable public RDP endpoints on virtual machines to connect to them - you can instead use the private IP addresses of your virtual private network to RDP to them through the secure VPN connection.
For details instructions on how to do all of the above please read our Tutorial on how to “Configure a Point-to-Site VPN in the Management Portal”
Software VPN Device support for Site-to-Site
With today’s release we are also adding software VPN device support to our existing ‘Site-to-Site VPN’ connectivity solution (which previously required you to use a hardware VPN device from Cisco or Juniper). Starting today we also now support a pure software based Windows Server 2012 ‘Site-to-Site’ VPN option. All you need is a vanilla Windows Server 2012 installation. You can then run download and run a PowerShell script from the Windows Azure Management Portal that enables the Routing and Remote Access Service (RRAS) on the Windows Server and configures a Site-To-site VPN tunnel and routing table on it. Sandrino Di Mattia has a step-by-step tutorial on how to do this here.
This allows you to enable a full site-to-site VPN tunnel that connects your on-premises network and machines to your virtual network within Windows Azure - without having to buy a hardware VPN device.
Dynamic DNS Support
With today’s release we have also relaxed restrictions around DNS server setting updates in virtual networks. You can now update the DNS server settings of a virtual network at any time without having to redeploy the virtual network and the VMs in them. Each VM in the virtual network will pick up the updated settings when the DNS is refreshed on that machine, either by renewing the DNS settings or by rebooting the instance. This makes updates much simpler.
If you’re interested further in Windows Azure Virtual Networks, and the capabilities and scenarios it enables, you can find more information here.
Virtual Machines: Remote PowerShell and Linux SSH provisioning enhancements
Last week we announced the general availability of Virtual Machine support as part of our IaaS release. With today’s update we are adding two nice enhancements:
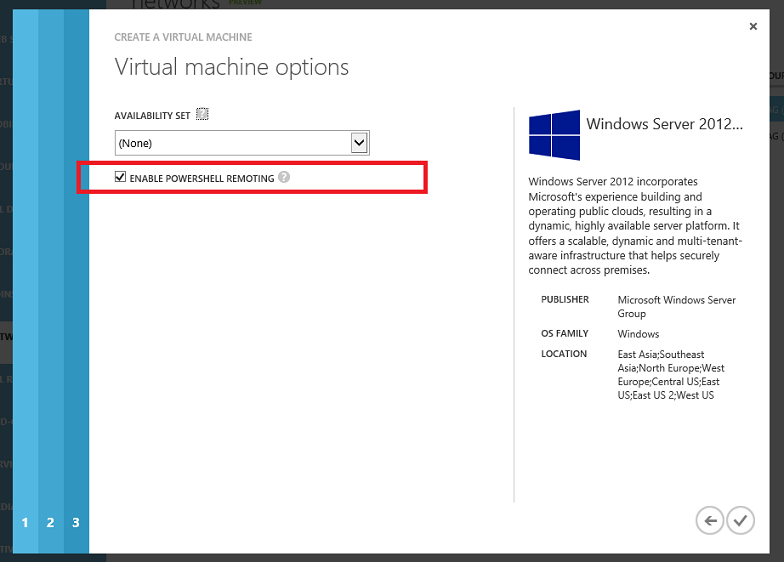
Support for Optionally Enabling Remote PowerShell on Windows Virtual Machines
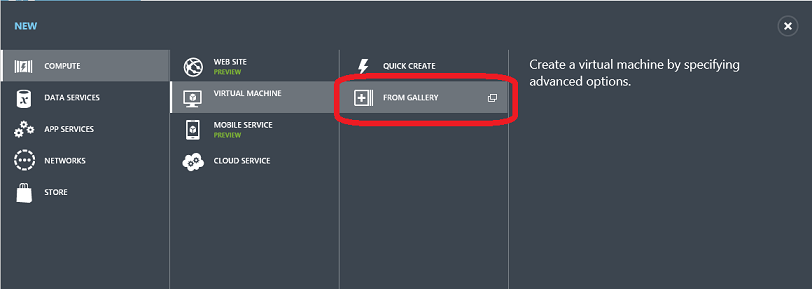
With today’s update, we now enable you to configure whether remote PowerShell is enabled for Windows VMs when you provision them using the Windows Azure Management Portal. This option is now available when you create a Virtual Machine using the FROM GALLERY option in the portal:
The last step of the wizard now provides a checkbox that gives you the option of enabling PowerShell Remoting:
When the checkbox is selected the VM enables remote PowerShell, and a default firewall endpoint is created for the deployment. This enables you to have the VM immediately configured and ready to use without ever having to RDP into the instance.
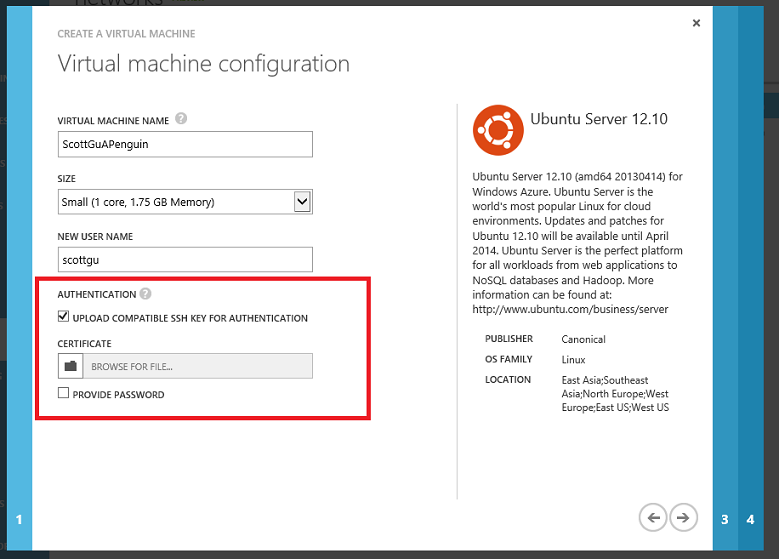
Linux SSH Provisioning
Previously, Linux VMs provisioned using Windows Azure defaulted to using a password as their authentication mechanism – with provisioning Linux VMs with SSH key-based authentication being optional. Based on feedback from customers, we have now made SSH key-based authentication the default option and allow you to omit enabling a password entirely if you upload a SSH key:
Cloud Services: Enabling Dynamic Remote Desktop for a Deployed Cloud Service
Windows Azure Cloud Services support the ability for developers to RDP into web and worker role instances. This can be useful when debugging issues.
Prior to today’s release, developers had to explicitly enable RDP support during development – prior to deploying the Cloud Service to production. If you forgot to enable this, and then ran into an issue in production, you couldn’t RDP into it without doing an app update and redeploy (and then waiting to hit the issue again).
With today’s release we have added support to enable administrators to dynamically configure remote desktop support – even when it was not enabled during the initial app deployment. This ensures you can always debug issues in production and never have to redeploy an app in order to RDP into it.
How to Enable Dynamic Remote Desktop on a Cloud Service
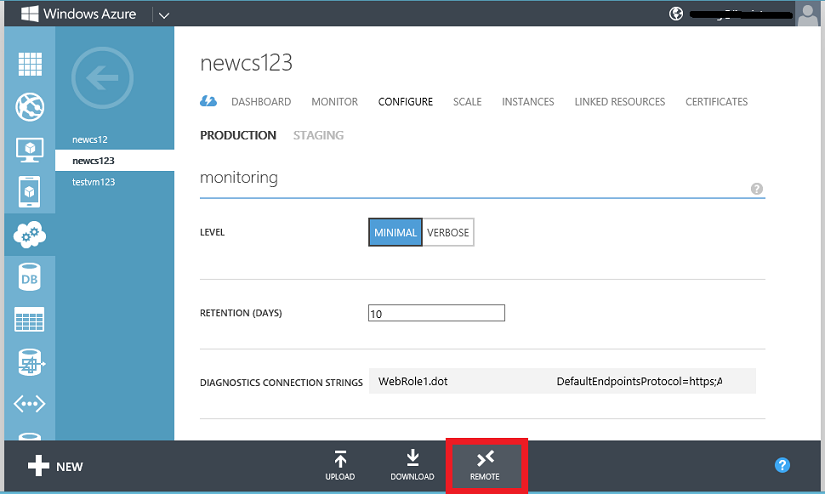
Remote desktop can be dynamically enabled for all the role instances of a Cloud Service, or enabled for an individual role basis. To enable remote desktop dynamically, navigate to the Configure tab of a cloud service and click on the REMOTE button:
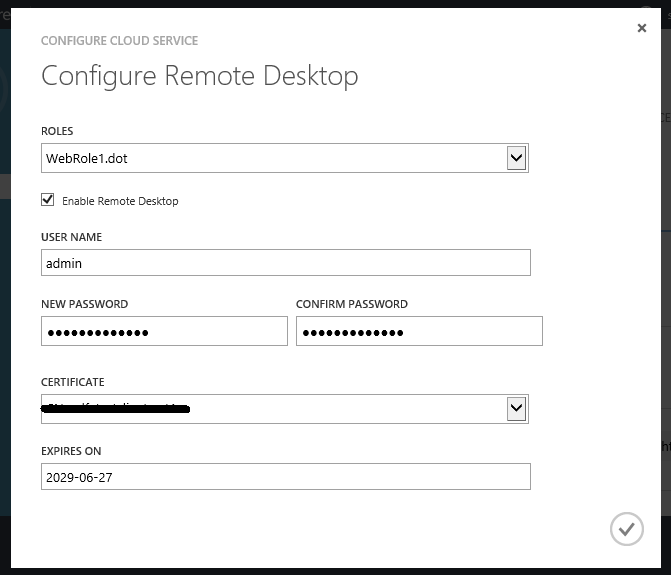
This will bring up a dialog that enables you to enable remote desktop – as well as specify a user/password to login into it:
Once dynamically enabled you can then RDP connect to any role instance within the application using the username/password you specified for them.
Windows Azure SDK for Ruby
Windows Azure already has SDKs for .NET, Java, Node.js, Python, PHP and Mobile Devices (Windows 8/Phone, iOS and Android). Today, we are happy to announce the first release of a new Windows Azure SDK for Ruby (v0.5.0).
Using our new IaaS offering you can already build and deploy Ruby applications in Windows Azure. With this first release of the Windows Azure SDK for Ruby, you can also now build Ruby applications that use the following Windows Azure services:
- Storage: Blobs, Tables and Queues
- Service Bus: Queues and Topics/Subscriptions
If you have Ruby installed, just do a gem install azure to start using it. Here are some useful links to learn more about using it:
Like all of the other Windows Azure SDKs we provide, the Windows Azure SDK for Ruby is a fully open source project hosted on GitHub. The work to develop this Ruby SDK was a joint effort between AppFog and Microsoft. I’d like to say a special thanks to AppFog and especially their CEO Lucas Carlson for their passion and support with this effort.
Summary
Today’s release includes a bunch of nice features that enable you to build even better cloud solutions. If you don’t already have a Windows Azure account, you can sign-up for a free trial and start using all of the above features today. Then visit the Windows Azure Developer Center to learn more about how to build apps with it.
Hope this helps,
Scott
P.S. In addition to blogging, I am also now using Twitter for quick updates and to share links. Follow me at: twitter.com/scottgu