Windows Azure: Backup Services Release, Hyper-V Recovery Manager, VM Enhancements, Enhanced Enterprise Management Support
This morning we released a huge set of updates to Windows Azure. These new capabilities include:
- Backup Services: General Availability of Windows Azure Backup Services
- Hyper-V Recovery Manager: Public preview of Windows Azure Hyper-V Recovery Manager
- Virtual Machines: Delete Attached Disks, Availability Set Warnings, SQL AlwaysOn Configuration
- Active Directory: Securely manage hundreds of SaaS applications
- Enterprise Management: Use Active Directory to Better Manage Windows Azure
- Windows Azure SDK 2.2: A massive update of our SDK + Visual Studio tooling support
All of these improvements are now available to use immediately. Below are more details about them.
Backup Service: General Availability Release of Windows Azure Backup
Today we are releasing Windows Azure Backup Service as a general availability service. This release is now live in production, backed by an enterprise SLA, supported by Microsoft Support, and is ready to use for production scenarios.
Windows Azure Backup is a cloud based backup solution for Windows Server which allows files and folders to be backed up and recovered from the cloud, and provides off-site protection against data loss. The service provides IT administrators and developers with the option to back up and protect critical data in an easily recoverable way from any location with no upfront hardware cost.
Windows Azure Backup is built on the Windows Azure platform and uses Windows Azure blob storage for storing customer data. Windows Server uses the downloadable Windows Azure Backup Agent to transfer file and folder data securely and efficiently to the Windows Azure Backup Service. Along with providing cloud backup for Windows Server, Windows Azure Backup Service also provides capability to backup data from System Center Data Protection Manager and Windows Server Essentials, to the cloud.
All data is encrypted onsite before it is sent to the cloud, and customers retain and manage the encryption key (meaning the data is stored entirely secured and can’t be decrypted by anyone but yourself).
Getting Started
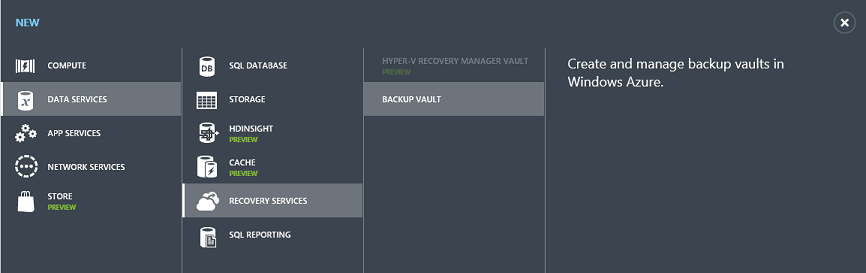
To get started with the Windows Azure Backup Service, create a new Backup Vault within the Windows Azure Management Portal. Click New->Data Services->Recovery Services->Backup Vault to do this:
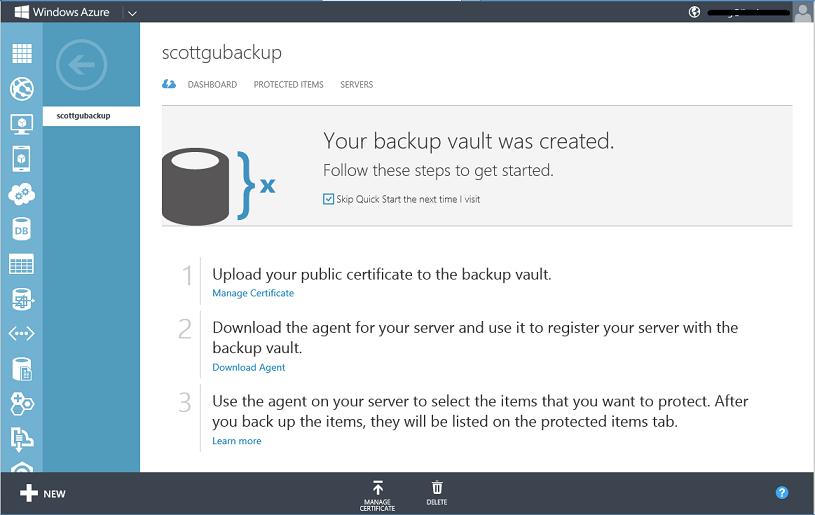
Once the backup vault is created you’ll be presented with a simple tutorial that will help guide you on how to register your Windows Servers with it:
Once the servers you want to backup are registered, you can use the appropriate local management interface (such as the Microsoft Management Console snap-in, System Center Data Protection Manager Console, or Windows Server Essentials Dashboard) to configure the scheduled backups and to optionally initiate recoveries. You can follow these tutorials to learn more about how to do this:
- Tutorial: Schedule Backups Using the Windows Azure Backup Agent This tutorial helps you with setting up a backup schedule for your registered Windows Servers. Additionally, it also explains how to use Windows PowerShell cmdlets to set up a custom backup schedule.
- Tutorial: Recover Files and Folders Using the Windows Azure Backup Agent This tutorial helps you with recovering data from a backup. Additionally, it also explains how to use Windows PowerShell cmdlets to do the same tasks.
Below are some of the key benefits the Windows Azure Backup Service provides:
- Simple configuration and management. Windows Azure Backup Service integrates with the familiar Windows Server Backup utility in Windows Server, the Data Protection Manager component in System Center and Windows Server Essentials, in order to provide a seamless backup and recovery experience to a local disk, or to the cloud.
- Block level incremental backups. The Windows Azure Backup Agent performs incremental backups by tracking file and block level changes and only transferring the changed blocks, hence reducing the storage and bandwidth utilization. Different point-in-time versions of the backups use storage efficiently by only storing the changes blocks between these versions.
- Data compression, encryption and throttling. The Windows Azure Backup Agent ensures that data is compressed and encrypted on the server before being sent to the Windows Azure Backup Service over the network. As a result, the Windows Azure Backup Service only stores encrypted data in the cloud storage. The encryption key is not available to the Windows Azure Backup Service, and as a result the data is never decrypted in the service. Also, users can setup throttling and configure how the Windows Azure Backup service utilizes the network bandwidth when backing up or restoring information.
- Data integrity is verified in the cloud. In addition to the secure backups, the backed up data is also automatically checked for integrity once the backup is done. As a result, any corruptions which may arise due to data transfer can be easily identified and are fixed automatically.
- Configurable retention policies for storing data in the cloud. The Windows Azure Backup Service accepts and implements retention policies to recycle backups that exceed the desired retention range, thereby meeting business policies and managing backup costs.
Hyper-V Recovery Manager: Now Available in Public Preview
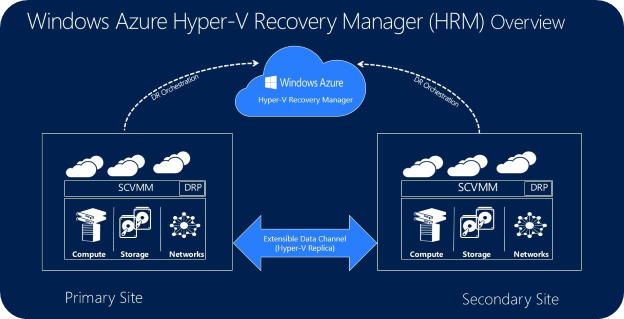
I’m excited to also announce the public preview of a new Windows Azure Service – the Windows Azure Hyper-V Recovery Manager (HRM).
Windows Azure Hyper-V Recovery Manager helps protect your business critical services by coordinating the replication and recovery of System Center Virtual Machine Manager 2012 SP1 and System Center Virtual Machine Manager 2012 R2 private clouds at a secondary location. With automated protection, asynchronous ongoing replication, and orderly recovery, the Hyper-V Recovery Manager service can help you implement Disaster Recovery and restore important services accurately, consistently, and with minimal downtime.
Application data in an Hyper-V Recovery Manager scenarios always travels on your on-premise replication channel. Only metadata (such as names of logical clouds, virtual machines, networks etc.) that is needed for orchestration is sent to Azure. All traffic sent to/from Azure is encrypted.
You can begin using Windows Azure Hyper-V Recovery today by clicking New->Data Services->Recovery Services->Hyper-V Recovery Manager within the Windows Azure Management Portal. You can read more about Windows Azure Hyper-V Recovery Manager in Brad Anderson’s 9-part series, Transform the datacenter. To learn more about setting up Hyper-V Recovery Manager follow our detailed step-by-step guide.
Virtual Machines: Delete Attached Disks, Availability Set Warnings, SQL AlwaysOn
Today’s Windows Azure release includes a number of nice updates to Windows Azure Virtual Machines. These improvements include:
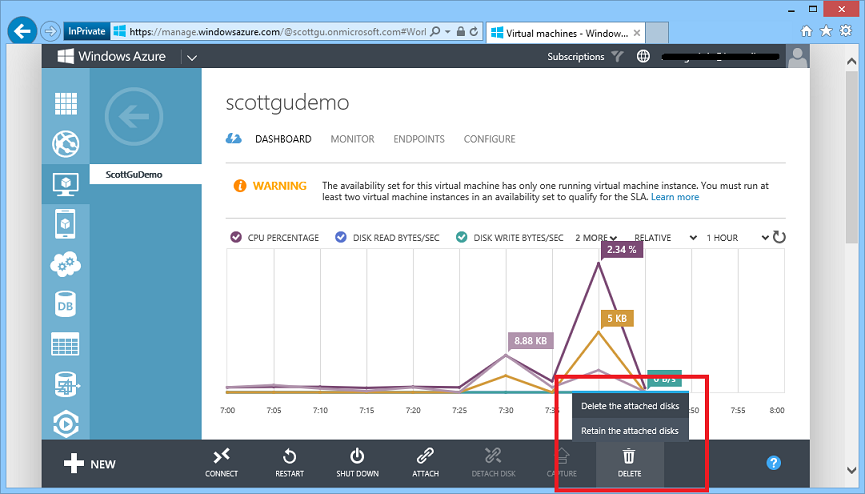
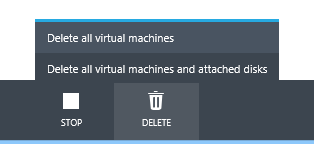
Ability to Delete both VM Instances + Attached Disks in One Operation
Prior to today’s release, when you deleted VMs within Windows Azure we would delete the VM instance – but not delete the drives attached to the VM. You had to manually delete these yourself from the storage account. With today’s update we’ve added a convenience option that now allows you to either retain or delete the attached disks when you delete the VM:
We’ve also added the ability to delete a cloud service, its deployments, and its role instances with a single action. This can either be a cloud service that has production and staging deployments with web and worker roles, or a cloud service that contains virtual machines. To do this, simply select the Cloud Service within the Windows Azure Management Portal and click the “Delete” button:
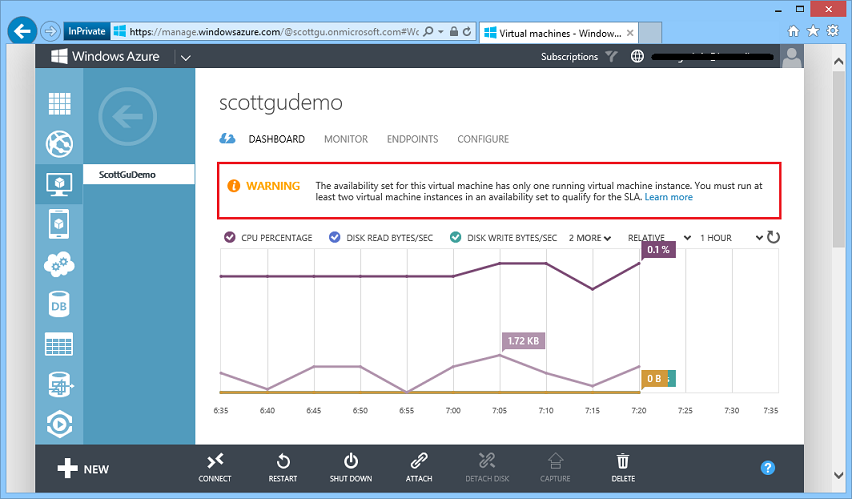
Warnings on Availability Sets with Only One Virtual Machine In Them
One of the nice features that Windows Azure Virtual Machines supports is the concept of “Availability Sets”. An “availability set” allows you to define a tier/role (e.g. webfrontends, databaseservers, etc) that you can map Virtual Machines into – and when you do this Windows Azure separates them across fault domains and ensures that at least one of them is always available during servicing operations. This enables you to deploy applications in a high availability way.
One issue we’ve seen some customers run into is where they define an availability set, but then forget to map more than one VM into it (which defeats the purpose of having an availability set). With today’s release we now display a warning in the Windows Azure Management Portal if you have only one virtual machine deployed in an availability set to help highlight this:
You can learn more about configuring the availability of your virtual machines here.
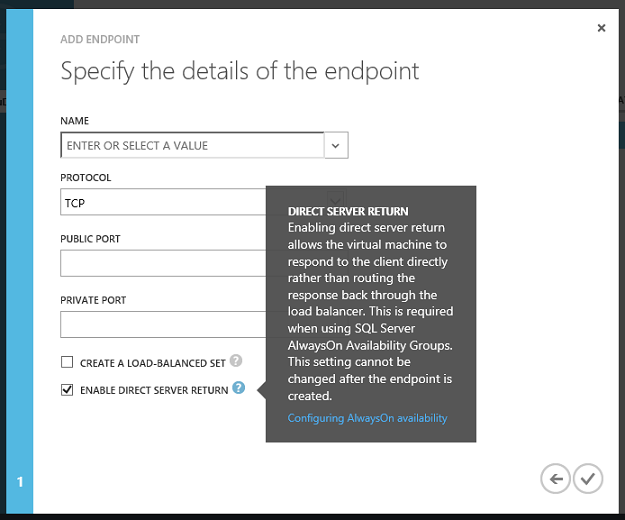
Configuring SQL Server Always On
SQL Server Always On is a great feature that you can use with Windows Azure to enable high availability and DR scenarios with SQL Server.
Today’s Windows Azure release makes it even easier to configure SQL Server Always On by enabling “Direct Server Return” endpoints to be configured and managed within the Windows Azure Management Portal. Previously, setting this up required using PowerShell to complete the endpoint configuration. Starting today you can enable this simply by checking the “Direct Server Return” checkbox:
You can learn more about how to use direct server return for SQL Server AlwaysOn availability groups here.
Active Directory: Application Access Enhancements
This summer we released our initial preview of our Application Access Enhancements for Windows Azure Active Directory. This service enables you to securely implement single-sign-on (SSO) support against SaaS applications (including Office 365, SalesForce, Workday, Box, Google Apps, GitHub, etc) as well as LOB based applications (including ones built with the new Windows Azure AD support we shipped last week with ASP.NET and VS 2013).
Since the initial preview we’ve enhanced our SAML federation capabilities, integrated our new password vaulting system, and shipped multi-factor authentication support. We've also turned on our outbound identity provisioning system and have it working with hundreds of additional SaaS Applications:
Earlier this month we published an update on dates and pricing for when the service will be released in general availability form. In this blog post we announced our intention to release the service in general availability form by the end of the year. We also announced that the below features would be available in a free tier with it:
- SSO to every SaaS app we integrate with – Users can Single Sign On to any app we are integrated with at no charge. This includes all the top SAAS Apps and every app in our application gallery whether they use federation or password vaulting.
- Application access assignment and removal – IT Admins can assign access privileges to web applications to the users in their active directory assuring that every employee has access to the SAAS Apps they need. And when a user leaves the company or changes jobs, the admin can just as easily remove their access privileges assuring data security and minimizing IP loss
- User provisioning (and de-provisioning) – IT admins will be able to automatically provision users in 3rd party SaaS applications like Box, Salesforce.com, GoToMeeting, DropBox and others. We are working with key partners in the ecosystem to establish these connections, meaning you no longer have to continually update user records in multiple systems.
- Security and auditing reports – Security is a key priority for us. With the free version of these enhancements you'll get access to our standard set of access reports giving you visibility into which users are using which applications, when they were using them and where they are using them from. In addition, we'll alert you to un-usual usage patterns for instance when a user logs in from multiple locations at the same time.
-
Our Application Access Panel – Users are logging in from every type of devices including Windows, iOS, & Android. Not all of these devices handle authentication in the same manner but the user doesn't care. They need to access their apps from the devices they love. Our Application Access Panel will support the ability for users to access access and launch their apps from any device and anywhere.
You can learn more about our plans for application management with Windows Azure Active Directory here. Try out the preview and start using it today.
Enterprise Management: Use Active Directory to Better Manage Windows Azure
Windows Azure Active Directory provides the ability to manage your organization in a directory which is hosted entirely in the cloud, or alternatively kept in sync with an on-premises Windows Server Active Directory solution (allowing you to seamlessly integrate with the directory you already have).
With today’s Windows Azure release we are integrating Windows Azure Active Directory even more within the core Windows Azure management experience, and enabling an even richer enterprise security offering. Specifically:
1) All Windows Azure accounts now have a default Windows Azure Active Directory created for them. You can create and map any users you want into this directory, and grant administrative rights to manage resources in Windows Azure to these users.
2) You can keep this directory entirely hosted in the cloud – or optionally sync it with your on-premises Windows Server Active Directory. Both options are free. The later approach is ideal for companies that wish to use their corporate user identities to sign-in and manage Windows Azure resources. It also ensures that if an employee leaves an organization, his or her access control rights to the company’s Windows Azure resources are immediately revoked.
3) The Windows Azure Service Management APIs have been updated to support using Windows Azure Active Directory credentials to sign-in and perform management operations. Prior to today’s release customers had to download and use management certificates (which were not scoped to individual users) to perform management operations. We still support this management certificate approach (don’t worry – nothing will stop working). But we think the new Windows Azure Active Directory authentication support enables an even easier and more secure way for customers to manage resources going forward.
4) The Windows Azure SDK 2.2 release (which is also shipping today) includes built-in support for the new Service Management APIs that authenticate with Windows Azure Active Directory, and now allow you to create and manage Windows Azure applications and resources directly within Visual Studio using your Active Directory credentials. This, combined with updated PowerShell scripts that also support Active Directory, enables an end-to-end enterprise authentication story with Windows Azure.
Below are some details on how all of this works:
Subscriptions within a Directory
As part of today’s update, we have associated all existing Window Azure accounts with a Windows Azure Active Directory (and created one for you if you don’t already have one).
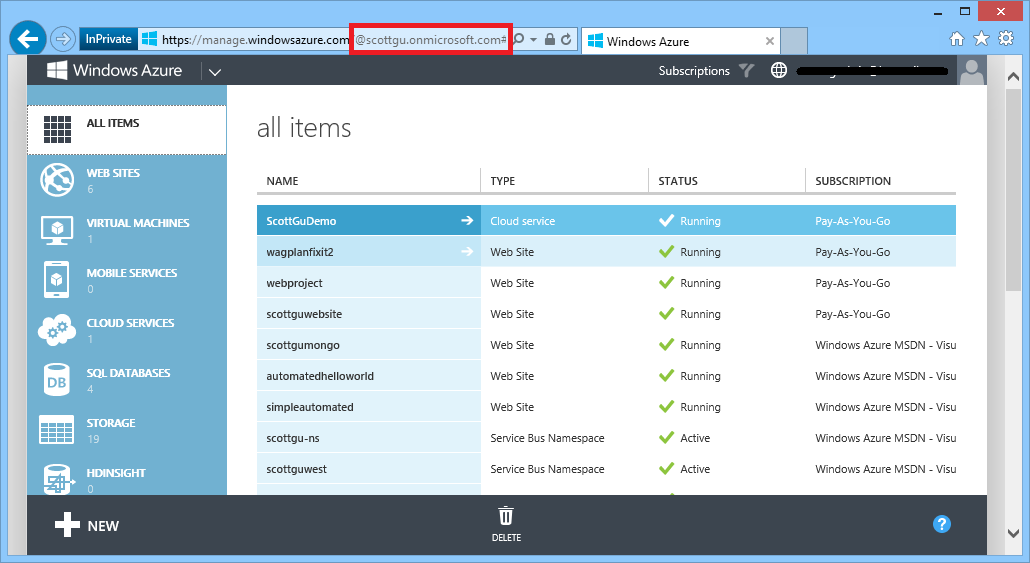
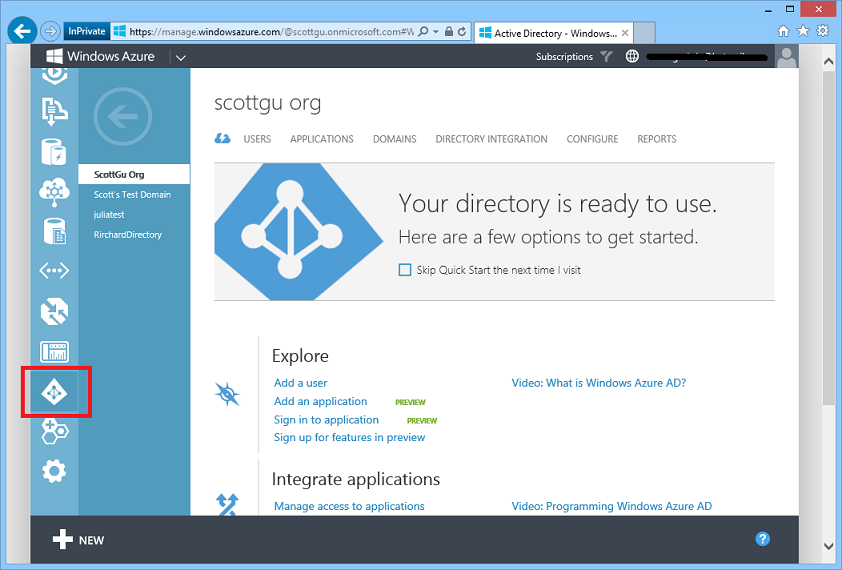
When you login to the Windows Azure Management Portal you’ll now see the directory name in the URI of the browser. For example, in the screen-shot below you can see that I have a “scottgu” directory that my subscriptions are hosted within:
Note that you can continue to use Microsoft Accounts (formerly known as Microsoft Live IDs) to sign-into Windows Azure. These map just fine to a Windows Azure Active Directory – so there is no need to create new usernames that are specific to a directory if you don’t want to. In the scenario above I’m actually logged in using my @hotmail.com based Microsoft ID which is now mapped to a “scottgu” active directory that was created for me. By default everything will continue to work just like you used to before.
Manage your Directory
You can manage an Active Directory (including the one we now create for you by default) by clicking the “Active Directory” tab in the left-hand side of the portal. This will list all of the directories in your account. Clicking one the first time will display a getting started page that provides documentation and links to perform common tasks with it:
You can use the built-in directory management support within the Windows Azure Management Portal to add/remove/manage users within the directory, enable multi-factor authentication, associate a custom domain (e.g. mycompanyname.com) with the directory, and/or rename the directory to whatever friendly name you want (just click the configure tab to do this). You can also setup the directory to automatically sync with an on-premises Active Directory using the “Directory Integration” tab.
Note that users within a directory by default do not have admin rights to login or manage Windows Azure based resources. You still need to explicitly grant them co-admin permissions on a subscription for them to login or manage resources in Windows Azure. You can do this by clicking the Settings tab on the left-hand side of the portal and then by clicking the administrators tab within it.
Sign-In Integration within Visual Studio
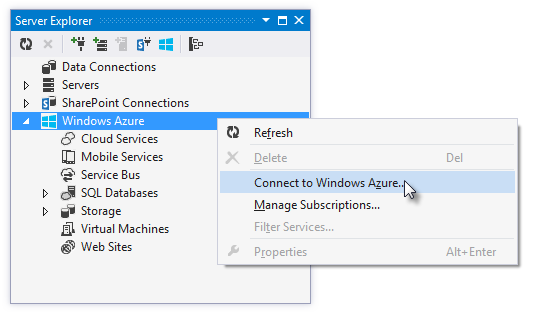
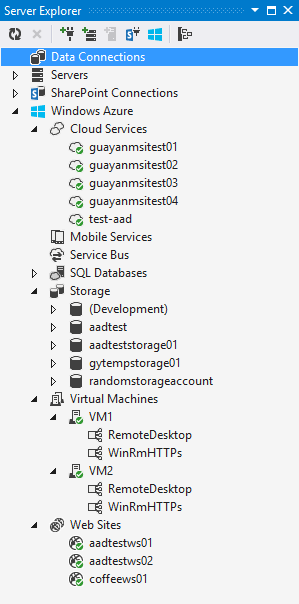
If you install the new Windows Azure SDK 2.2 release, you can now connect to Windows Azure from directly inside Visual Studio without having to download any management certificates. You can now just right-click on the “Windows Azure” icon within the Server Explorer and choose the “Connect to Windows Azure” context menu option to do so:
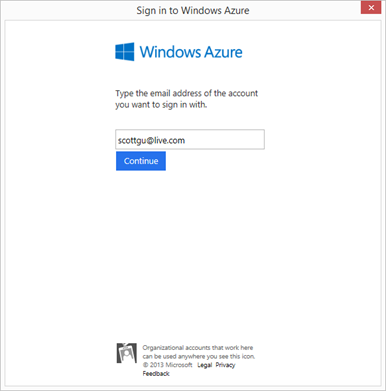
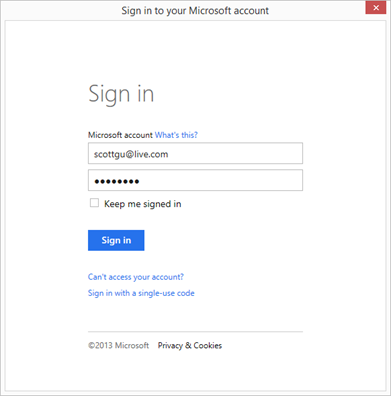
Doing this will prompt you to enter the email address of the username you wish to sign-in with (make sure this account is a user in your directory with co-admin rights on a subscription):
You can use either a Microsoft Account (e.g. Windows Live ID) or an Active Directory based Organizational account as the email. The dialog will update with an appropriate login prompt depending on which type of email address you enter:
Once you sign-in you’ll see the Windows Azure resources that you have permissions to manage show up automatically within the Visual Studio server explorer and be available to start using:
No downloading of management certificates required. All of the authentication was handled using your Windows Azure Active Directory!
Manage Subscriptions across Multiple Directories
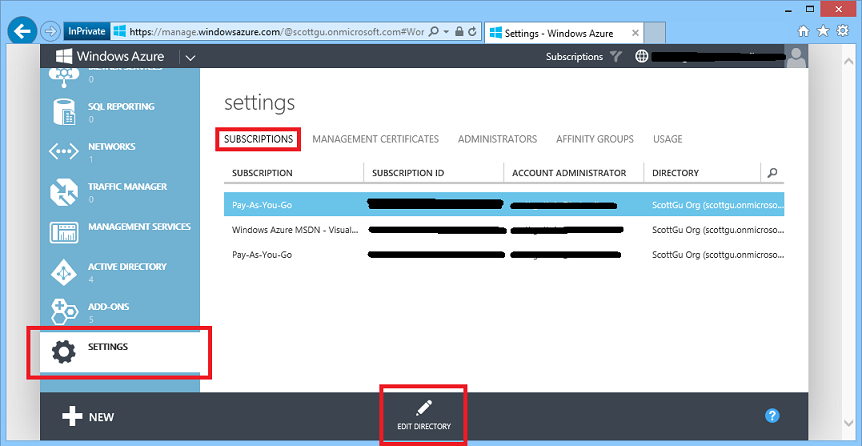
If you have already have multiple directories and multiple subscriptions within your Windows Azure account, we have done our best to create a good default mapping of your subscriptions->directories as part of today’s update. If you don’t like the default subscription-to-directory mapping we have done you can click the Settings tab in the left-hand navigation of the Windows Azure Management Portal and browse to the Subscriptions tab within it:
If you want to map a subscription under a different directory in your account, simply select the subscription from the list, and then click the “Edit Directory” button to choose which directory to map it to. Mapping a subscription to a different directory takes only seconds and will not cause any of the resources within the subscription to recycle or stop working. We’ve made the directory->subscription mapping process self-service so that you always have complete control and can map things however you want.
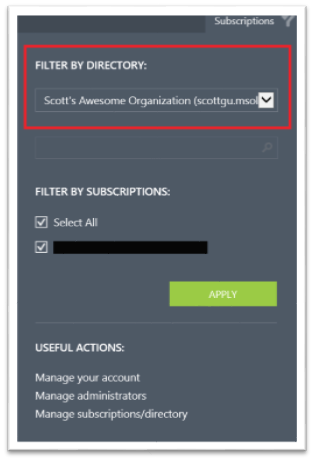
Filtering By Directory and Subscription
Within the Windows Azure Management Portal you can filter resources in the portal by subscription (allowing you to show/hide different subscriptions). If you have subscriptions mapped to multiple directory tenants, we also now have a filter drop-down that allows you to filter the subscription list by directory tenant. This filter is only available if you have multiple subscriptions mapped to multiple directories within your Windows Azure Account:
Windows Azure SDK 2.2
Today we are also releasing a major update of our Windows Azure SDK. The Windows Azure SDK 2.2 release adds some great new features including:
- Visual Studio 2013 Support
- Integrated Windows Azure Sign-In support within Visual Studio
- Remote Debugging Cloud Services with Visual Studio
- Firewall Management support within Visual Studio for SQL Databases
- Visual Studio 2013 RTM VM Images for MSDN Subscribers
- Windows Azure Management Libraries for .NET
- Updated Windows Azure PowerShell Cmdlets and ScriptCenter
I’ll post a follow-up blog shortly with more details about all of the above.
Additional Updates
In addition to the above enhancements, today’s release also includes a number of additional improvements:
- AutoScale: Richer time and date based scheduling support (set different rules on different dates)
- AutoScale: Ability to Scale to Zero Virtual Machines (very useful for Dev/Test scenarios)
- AutoScale: Support for time-based scheduling of Mobile Service AutoScale rules
- Operation Logs: Auditing support for Service Bus management operations
Today we also shipped a major update to the Windows Azure SDK – Windows Azure SDK 2.2. It has so much goodness in it that I have a whole second blog post coming shortly on it! :-)
Summary
Today’s Windows Azure release enables a bunch of great new scenarios, and enables a much richer enterprise authentication offering.
If you don’t already have a Windows Azure account, you can sign-up for a free trial and start using all of the above features today. Then visit the Windows Azure Developer Center to learn more about how to build apps with it.
Hope this helps,
Scott
P.S. In addition to blogging, I am also now using Twitter for quick updates and to share links. Follow me at: twitter.com/scottgu