Azure Bastion
Microsoft recently announced public preview of Azure Bastion, a managed PaaS service which provides RDP and SSH connectivity through a browser to access Azure VMs. It eliminates the need of a public IP address assign to the VM. Azure Bastion is deployed in the Virtual Network and provides RDP/SSH provision for all the VMs in the same Virtual Network.

Source – Microsoft Docs
What is needed
- Azure VM
- Subnet in the Virtual Network using the name value “AzureBastionSubnet”
- Microsoft Edge or Google Chrome
What is not needed
- Public IP Address on Azure VM
- RDP or SSH Client
- Agent on Azure VM
- NSGs
- Jump box
Use the Azure portal - preview instead of the regular Azure portal to create the service. The preview is limited only to certain Azure public regions currently.
Set up Azure Bastion for an existing VM
Create a subnet with the name “AzureBastionSubnet” in the Virtual Network. It is recommended to use at least a /27 or larget subnet.

Search for “Bastion (preview)” from Microsoft.
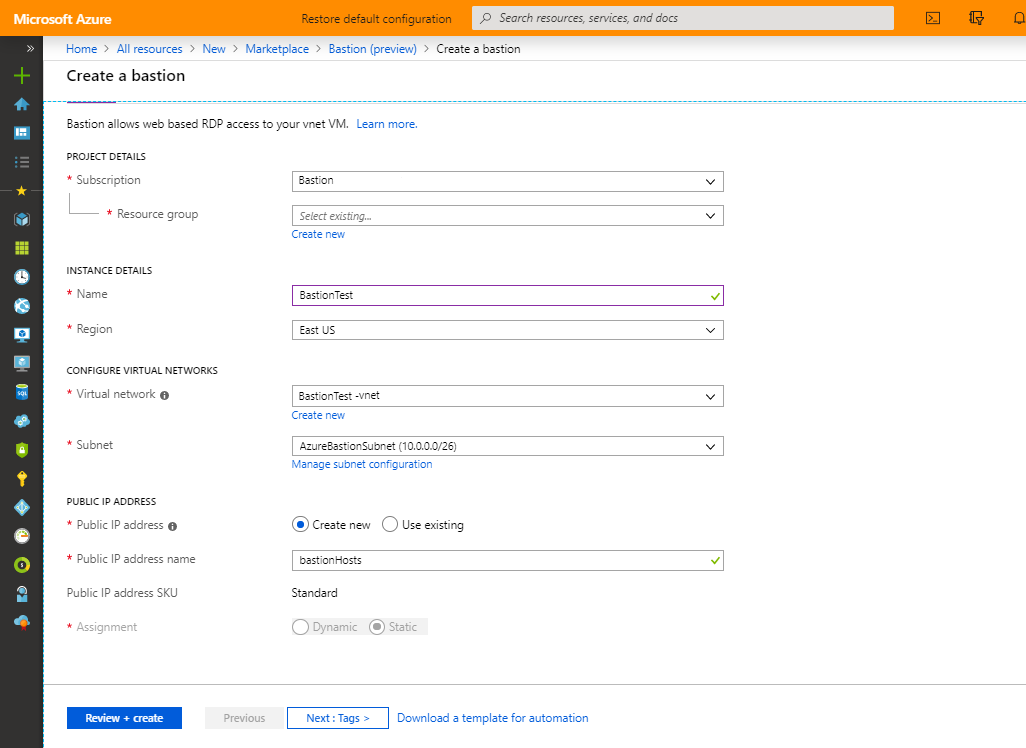
Specify the configuration settings and create the resource
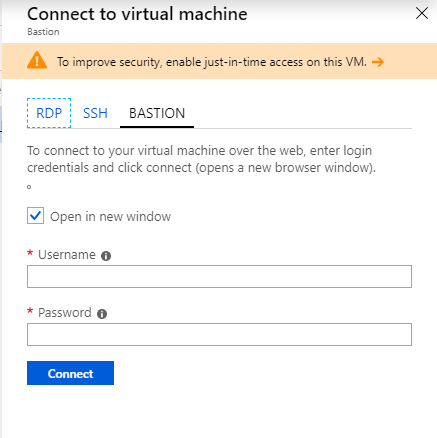
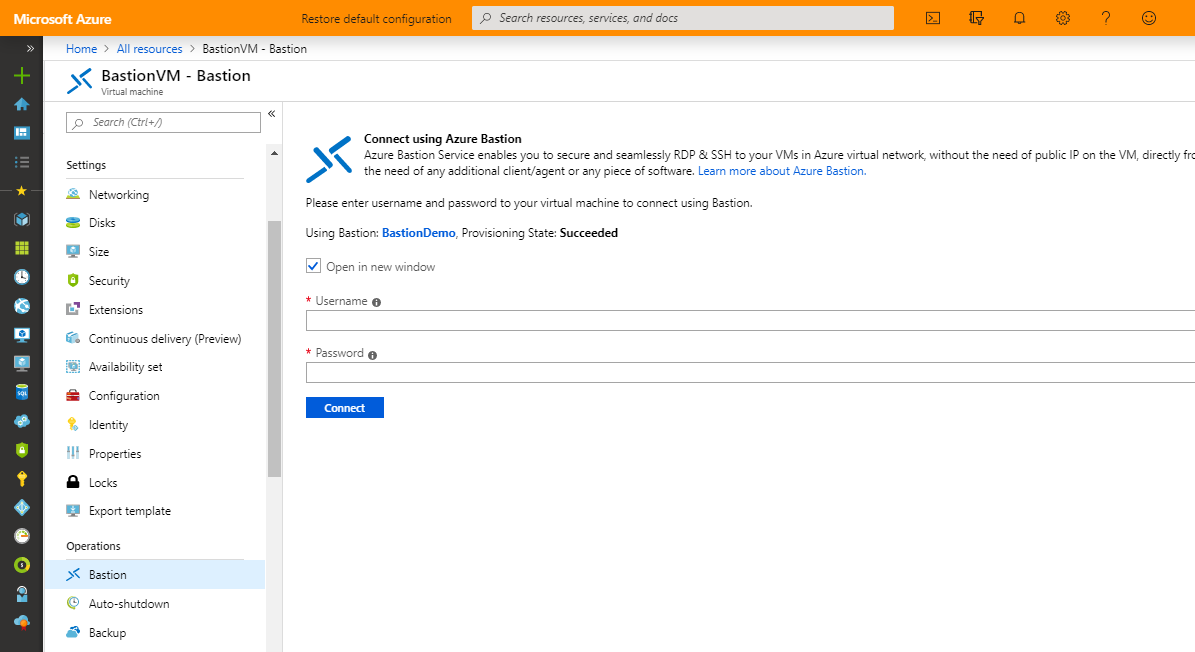
You can either click on the “connect” from the VM’s overview page or use the “Bastion” option listed under the “Operations” section of the VM.
Road ahead
- Azure Active Directory Integration
- Single Sign-on, Azure Multi-Factor Authentication
- Two factor authentication for RDP/SSH connection
- Support for native RDP/SSH Clients
- Privilege Identity Management Integration
- Remote App Streaming
- Support for peered virtual networks
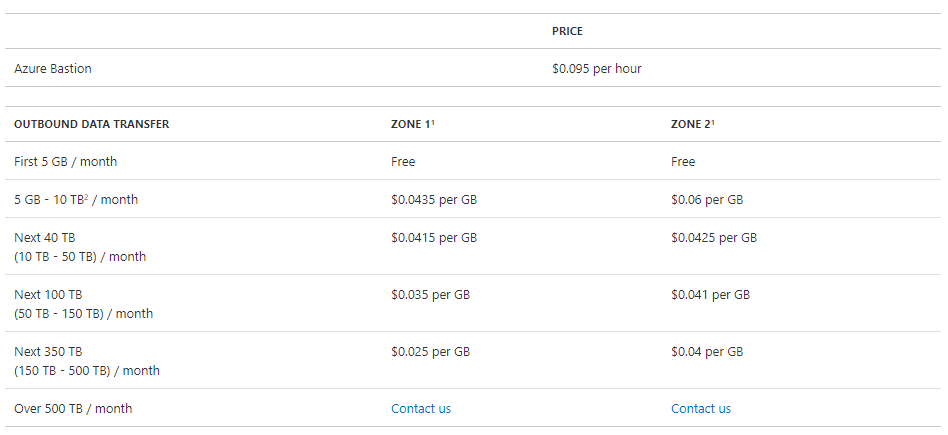
Pricing
The pricing for this service is per hour and it is an “always on” service as of now.
References
https://azure.microsoft.com/en-in/blog/announcing-the-preview-of-microsoft-azure-bastion/